Microsoft with Azure Sphere Looks to Set Gold Standard in End-to-End IoT Security
Traditionally, security circled around securing network and software applications. However, as more devices get connected to the internet, and threats rise, there is an unprecedentedneed to secure hardwarealongside the data flow from edge devices to the cloud. Hence, integrating security across all four layers (hardware, software, network, and cloud) becomes vital for a secure IoT deployment. We are already seeing this being adopted across data-centric devices such assmartphones.
What are the options to enable hardware security?
The key is to secure the hardware at the chipset (MCU/SoC) level to first secure the data flowing through the internal bus. This can be done by embedding Secure Elements (SE) such as Physical Unclonable Function PUFs, Trusted Platform Module (TPMs), or Hardware Security Module (HSM) to the system within the devices. Further, key injection in the secure enclave/PUF along with cryptographic key management to ensure the secure identity of the devices and to create secure tunneling of data flowing within the device and then from the device to the cloud.
How will secure hardware help Microsoft?
Microsoft is theleading end-to-end IoT platformprovider globally connecting millions of edge IoT devices across tens of thousands of enterprises to its Azure cloud via its Azure IoT platform. Microsoft also has been offering Azure Edge IoT software to enable computing and intelligent decision making at the edge. As a result, Microsoft must ensure the millions of devices running its Azure instances are not compromised and securely connected to its cloud.
In light of this, Microsoft has been looking to build secure chips with silicon partners to create a “hardware-based root of trust”. This will helpsolve cloning and counterfeit issuesand will also establishsecure authenticationwith its IoT hub platform via aunique trusted identity.
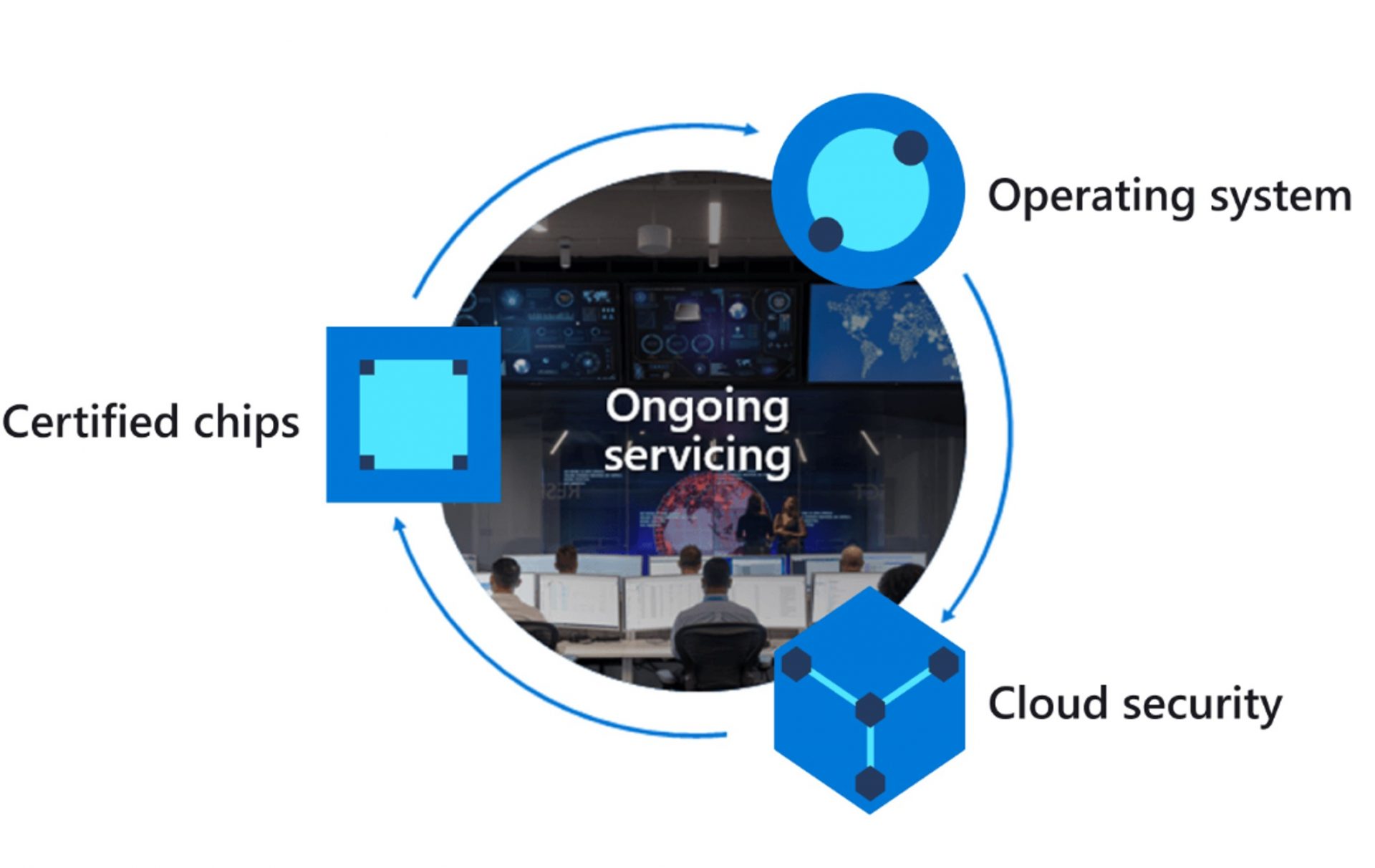
To achieve this goal, back in 2018, Microsoftannounced Azure Sphereto build multi-layered end-to-end security. Since then Microsoft Azure Sphere has evolved and constitutesthree key elements:
Source: Microsoft
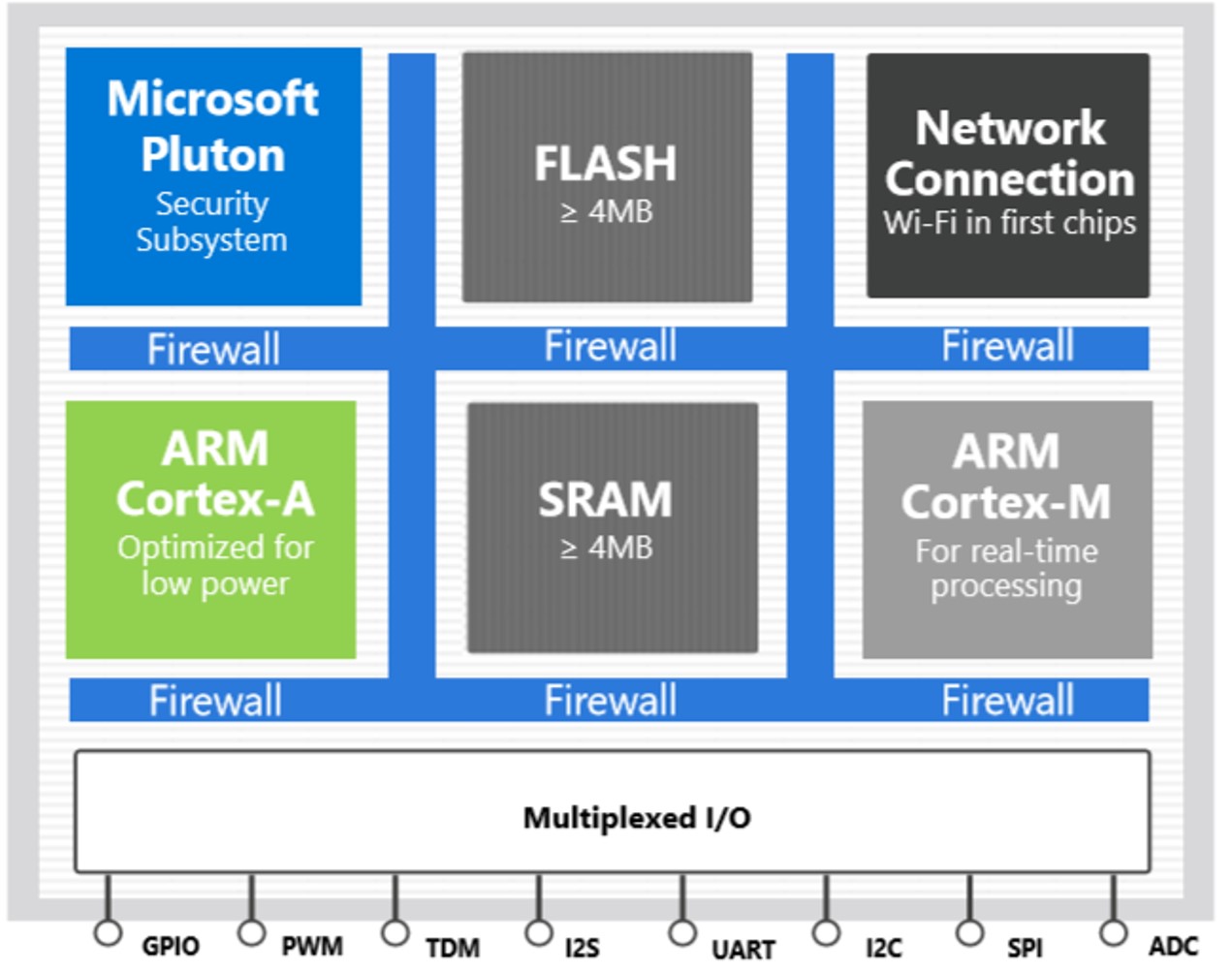
- Hardware: Azure Sphere embeds secure keys (public) within asecure MCU/MPUpowered by itsPlutonsecurity subsystem.
- Pluton includes a security processor unit with a random number generator (RNG)
- Tamper and side-channel attack resistant
- Other cryptography and encryption tools
- Secure booting for remote attestation and certificate-based security
As an example, the MediaTek MT3620 contains an isolated security subsystem with its own Arm Cortex-M4F core that handles secure boot and secure system operation. This M4F security processor features a 128kB secured TCM and a 64kB secured mask ROM bootloader.
 Source: Microsoft
Source: Microsoft
- Software:Azure Sphere OS:
- Azure Sphere OS is made up of a custom Linux kernel, which runs on 2.4MB code storage, which is carefully tuned for the flash and RAM footprint of the Azure Sphere MCU to reduce its attack surface.
- 操作系统与Azure通信安全范围service in the cloud for secure device authentication, network management, application management for all outbound traffic.
- It undertakes secure monitoring to protect memory, flash and other MCU resources limiting exposure.
- The OS includes Microsoft-provided application runtime to restrict access to file I/O or shell access.
- It also includes a high-level application platform which is signed by Microsoft Certificate Authority (CA) through a trusted pipeline to maintain all software other than the device-specific applications.
- Cloud:Azure Sphere Security Service
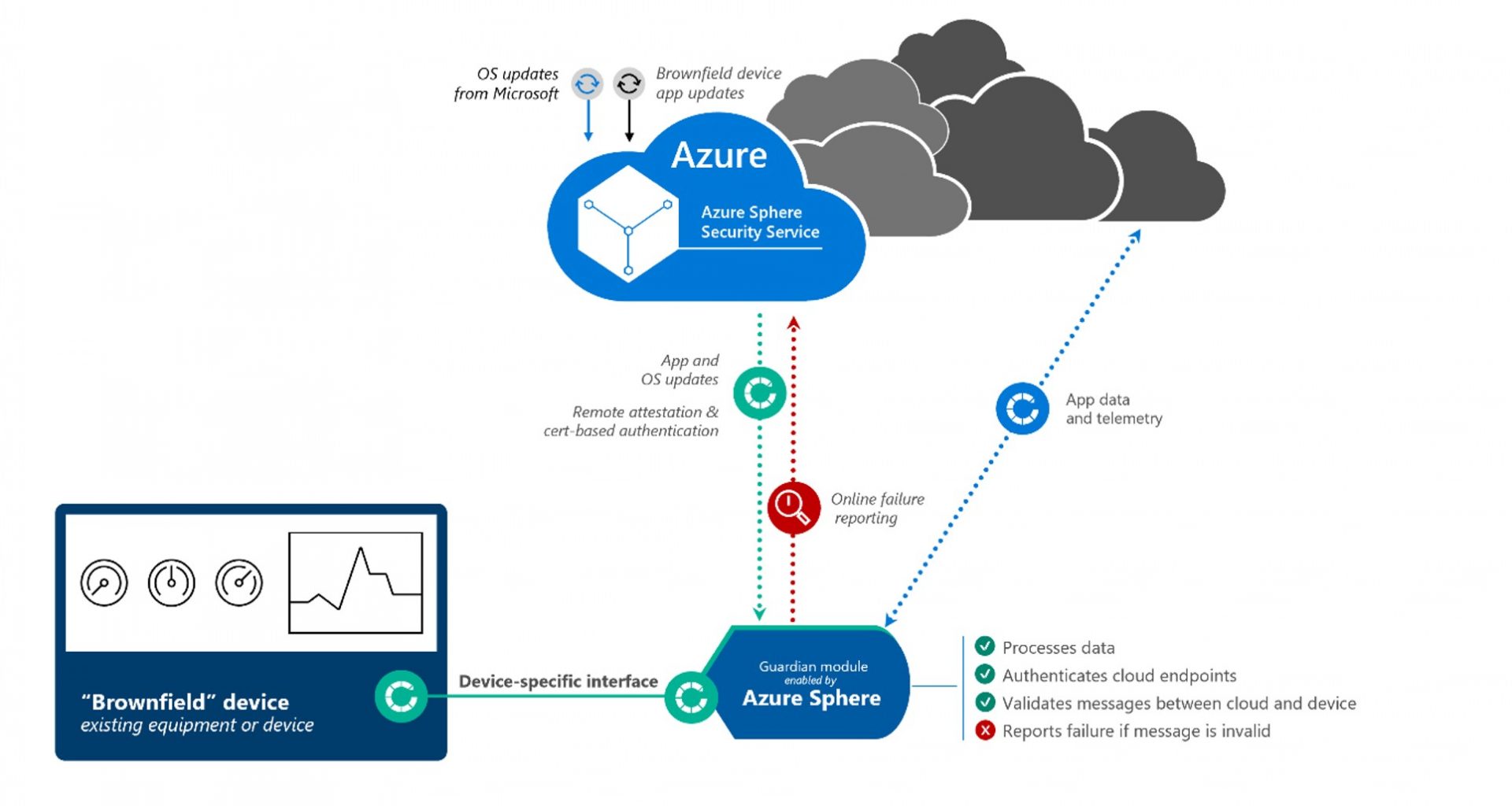
- Azure Sphere Security Servicebrokers trustfor device-to-cloud communication, detects threats, and renews device security viaCA based-authentication,failure reportingand automatic updates for OS.
- Azure Sphere in the cloud thus embeds with a private key that enablesasymmetric encryptionandauthenticates deviceswith paired public keys at the time of the manufacturing process.
- Further,Azure Sentinelprovides cloud security through Artificial Intelligence.
The integration of all three elements enablesthe hardware root of trust with asymmetric encryption. Further, it creates asecure tunnelfor the secure flow of data from chip to cloud ensuring both the data security atrestand intransit.
Following chart depicts Azure Sphere running on a Guardian IoT module for a brownfield IoT deployment
Source: Microsoft
Growing Partner Ecosystem:
- Chipsets:
- In 2018,ST Micro’sSTM32, a secure MCU embed with a secure element and integrated with Azure IoT C SDK, which enables direct and secure connectivity to the Azure IoT Hub, as well as full support for Azure device management.
- In mid-2019,NXP’sMX系列8,集成了微软Azure的球体ecurity architecture and Pluton Security Subsystem.
- MediaTek MT3620 is Azure Sphere ready
- At the end of 2019,Qualcomm’s9205 LTE multimode modem supporting both LTE-M / NB-IoT was integrated with Microsoft’s Azure Sphere.
- Modules
- Avnetandqiiooffer Avnet Guardian 100 and qiio q200 Guardian (add-on)modulesfor retrofitting on exiting brownfield devices which lack connectivity and security but need to be connected to the Internet.
- Other modules includeAvnetAES-MS-MT3620,AI-LinkWF-M620-RSC1 andUSIWi-Fi module with Bluetooth option.
With this approach, Microsoft is building a highly scalable and secure approach to onboard, manage and connect IoT devices and ensure the data is securely transmitted from device to cloud. This eliminates the need for most IoT customers to hire expensive security professionals.
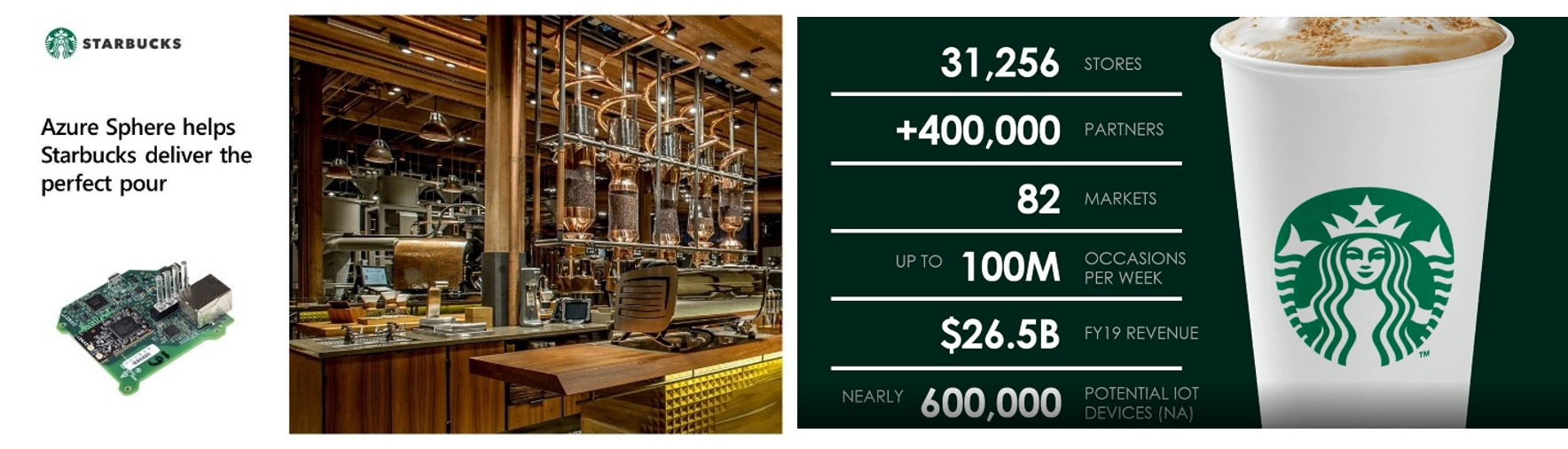
Case Study: Starbucks
Starbucks has deployed Azure Sphere across its stores in North America. Each Starbucks store has around ten to twelve pieces of equipment that are operational for more than fifteen hours a day and are needed to be connected to the cloud for beverage related data (10 to 12 data points worth 5MB generated per beverage), asset monitoring and any predictive maintenance to avoid disruptions. This is important as any equipment breakdown is directly proportional to the store’s performance, its business and customer dissatisfaction. Starbucks has therefore been using the guardian modules deployed by Azure Sphere with the help of Microsoft across all its brownfield equipment to securely connect and aggregate the data to the cloud.
Source: Microsoft
Chip-to-Cloud Security is the Gold Standard
Security andprivacyare global concerns around IoT, irrespective of country. Security is one of the major roadblocks for IoT. However, in the past two years, we have seen theadoptionof chip-to-cloud security due to an increase in awareness of the threats and its scalable solution. The end-to-end security will be critical to the success of any future IoT deployments to protect the asset as well as the data which, in most cases, is even more valuable.



 Source: Microsoft
Source: Microsoft